Every spring, BakerHostetler collects, analyzes, and compares key metrics on the incident response matters we handled in the prior year. The output – our Data Security Incident Response (DSIR) Report – highlights key findings and trends across these matters, as well as insights geared toward helping companies develop or bolster their cybersecurity measures, incident response plans, and information governance practices.
Our 2024 DSIR Report includes data on the more than 1,150 incidents we helped clients manage in 2023. The heart of the report – the data – can be found in the first several pages. Below we’ve highlighted some key findings from these initial sections.
Network Intrusions
Network intrusions continue to be the leading type of incident our clients experience. They are so prevalent, the 2024 DSIR Report included two new callouts specific to network intrusions:
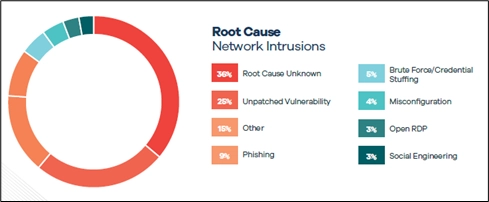

Almost three-fourths of the network intrusion matters we handled in 2023 involved deployment of ransomware. However, companies have become more resilient – our clients are detecting and recovering from incidents faster than in prior years. Additionally, while the average ransom paid has continued to increase ($747,651 in 2023 vs. $600,688 in 2022), our clients are paying less often (27 percent in 2023 vs. 40 percent in 2022).
- Faster Detection. Over half of our clients that experienced a network intrusion in 2023 had an endpoint detection and response (EDR) tool deployed. In matters where an EDR tool was present, incident detection occurred 40 percent faster than in those where one wasn’t in place. But keep in mind – simply purchasing and deploying an EDR tool is not enough and ensuring proper configuration is critical. Almost a third of our clients that responded to a network intrusion in 2023 learned that the EDR tool they had in place was either not in enforcement mode or didn’t have the anti-uninstall feature enabled.
- Slower Containment. One area where companies regressed is in the average time from detection of a network intrusion to containment (five days in 2023 vs. three days in 2022). This is due, in part, to the increased prevalence of Scattered Spider, a group known for gaining access through social engineering of help desk employees and “living off the land” – leveraging an organization’s own tools instead of using their own malware. Scattered Spider is also known to attempt to get back into an organization’s network even after containment measures have begun, making it more difficult – and more time-consuming – to fully contain an incident.
- Faster Recovery. Having the tools in place to allow for faster detection of an incident also allows for faster recovery. Some clients detected a network intrusion before encryption occurred, thanks to their EDR solution. Companies have also improved their backup solutions – air gapped, immutable, and up-to-date – which has, in turn, made them more resilient following an incident. Network segmentation has also proven critical, as it can prevent the spread of encryption by controlling data flows between (and access to) sub-networks.
Threat Actor Sophistication
While companies are implementing more and stronger safeguards, threat actors continue to adapt – finding new (or repurposing old) methods to bypass security controls and gain access. It’s a classic game of Whac-A-Mole. Despite multi-factor authentication, business email compromises were once again the second-most-common type of incident we handled in 2023. We saw several incidents involving a threat actor calling a help desk to reset a user password. In all of these matters, the threat actor successfully answered the help desk’s verification questions (confirming user’s date of birth, last four of SSN) and the password was reset. We also saw threat actors send phishing emails as .rpmsg emails, which can bypass even the most conservative spam filters. To combat these ever-evolving strategies, organizations can augment existing email security controls by taking the following steps:

Other Findings of Note
- Vendor Incidents Increase Significantly. Thanks in large part to the May 2023 incident at SFTP provider MOVEit, the number of incidents that occurred at a third-party vendor increased from 16 percent in 2022 to 25 percent in 2023. Read again: One-fourth of the incidents we handled in 2023 were vendor related. Given recent high-profile incidents at Change Healthcare, Ascension, and other organizations, we don’t expect this metric to deviate much, if at all, in next year’s report. Obviously, vetting your organization’s potential vendors is critical. But what we’ve found to be equally important (and often overlooked) is re-vetting – exercising ongoing diligence by requesting updated security risk assessments, reviewing contracts for necessary updates, and confirming your company’s data is not retained longer than necessary.
- Size of Notice Population. The number of incidents that result in notification has largely remained the same, with notice occurring in about 40-45 percent of our matters. What has changed, however, is the average number of individuals being notified (98,504 in 2023 vs. 47,851 in 2022). Threat actors know where to look to find and take files rich in personal information, leading to larger notification populations. Organizations should take the opportunity now to remove old, unneeded files containing personal or sensitive information, and should revisit their business processes to determine whether certain types of information are actually needed – for example, don’t create reports containing full SSNs unless it is absolutely necessary. Reducing the number of files and the amount of personal information contained within those files will help mitigate the impact of a data security incident if one occurs.
- Cost of Forensic Investigations. Looking at the 20 largest network intrusion matters handled in 2023, the average cost decreased by nearly $200,000 between 2022 and 2023 ($354,474 in 2023 vs. $550,987 in 2022). Again, pre-incident, widespread deployment of an EDR tool is to thank. Companies that don’t have this type of tool deployed prior to an incident often resort to licensing an EDR tool from the forensic firm, which, in large environments, can add anywhere from $50,000 to $100,000 per month to the total cost of an investigation.
[View source.]