 The 2021 edition of BakerHostetler’s annual Data Security Incident Response Report – a report based on the firm’s experience with data security incident response and litigation over the past year – features a number of important insights previously covered on this blog including trends in global breach notification, healthcare industry risks and ransomware.
The 2021 edition of BakerHostetler’s annual Data Security Incident Response Report – a report based on the firm’s experience with data security incident response and litigation over the past year – features a number of important insights previously covered on this blog including trends in global breach notification, healthcare industry risks and ransomware.
The Report is a helpful tool for companies to identify and respond to trends in data privacy and security, especially as it relates to litigation, enforcement and risk management. But, while this may not be as obvious, the data privacy and security risk trends identified in the Report have also impacted general corporate transactions. Many different types of transactions, from M&A to product/service development to standard commercial service agreements, have been impacted by the data privacy and security trends highlighted in the Report. In this series, we’ll look at how some of the trends highlighted in the Report have had an impact on commercial transactions over the past year, and at some of the key data privacy and security sensitivities for businesses considering or involved in these transactions.
Data Privacy and Security in M&A
Data privacy and security representations in M&A transaction documents is not a new concept. These days, most deals at least address data privacy and security in the representations in the merger transaction documents, typically in the form of seller representations regarding compliance with privacy laws and lack of privacy and security disputes. However, over the past couple of years, the detail in these representations, along with the attention paid to this topic during diligence, negotiation and post-closing transition, has moved this once remote deal consideration front and center. And this is not just for asset purchases of technology companies or where data and servers are included in the purchased assets; this trend has also applied to equity transactions and mergers in industries other than technology. As detailed below, this is driven, in part, by some of the trends identified in the Report.
Ransomware Prevalence and Cost
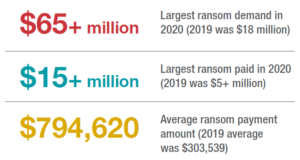

The increasing prevalence and cost of ransomware is driving the increased attention to data privacy and security in M&A. As highlighted in the Report, the surge of ransomware from 2019 has continued, and the number of high-profile ransomware attacks in the past year alone is alarming. The ransomware one-two punch of business continuity impact and potential theft of data with a threat to release the data publicly if the ransom is not paid can be especially devastating for businesses. In light of this, ransomware has (understandably) become a major concern for many businesses. Further, alerts and guidance from government agencies on ransomware preparedness and response has added to the complexity of this issue.
In the M&A context, the surge of ransomware has had several implications:
- Buyers want to know more about the data assets of the target. Sellers and target companies should be prepared to answer questions about data storage and use, data mapping, and deletion policies. As highlighted in the Key Findings of the Report, “[o]ld data on a file server is the most common source of notice obligations in ransomware matters.” If you don’t need the data, get rid of it (or the buyer may ask you to).
- Buyers want to know more about the IT architecture and policies of the target. Sellers and target companies should be prepared to answer questions about IT infrastructure, technical and organization security measures in place, and training and education procedures (especially phishing and ransomware training).
- The parties should consider IT risks during the post-closing transition and address cybersecurity in any applicable transition services agreement, especially network or data segregation if shared services are contemplated.
- If the target has been subject to a recent ransomware attack, there may be substantial follow-up regarding the target’s response to that incident (e.g., whether the ransom was paid, the applicability of insurance coverage, the impact on the target’s backups, the threat actor group and/or variant, whether law enforcement was involved, etc.).
- Each party should have an incident response plan that contemplates a ransomware incident.
Today, most organizations are aware of the risk of ransomware and the need to prepare for an event. But organizations that have not experienced a ransomware event are uncertain about what actually occurs, which hinders preparation and can raise questions during diligence. Building a ransomware playbook and conducting a tabletop exercise facilitated by a person experienced in responding to ransomware events are good preparation measures for sellers and buyers.
Vendor and Supply Chain Incidents Abound
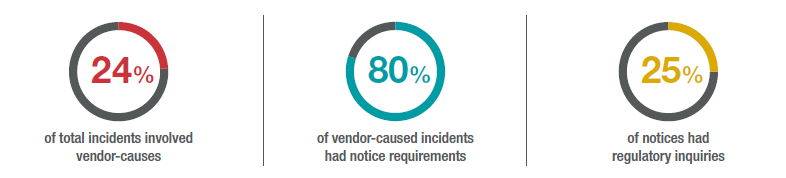
High-profile compromises of third-party service providers including SolarWinds, Blackbaud, finastra and Shopify, as well as compromises resulting from the exploitation of vulnerabilities in vendor software (Accellion in 2020 and Microsoft Exchange in 2021), have put cybersecurity-supply chain risk management (C-SCRM) front and center. C-SCRM and vendor compromises will only become more challenging as organizations rely more on third parties and threat actors see how effective these attacks can be.
This is further complicated by the proliferation of supply chain attacks over the past few years. Supply chain attacks have increased sharply over the past decade, and that trend continued in 2020 and early 2021. Supply chain attacks have obvious appeal to attackers and will keep happening.
In light of these risks, vendor management has become an integral part of the M&A process – both with respect to the buyer and seller as individual businesses and with respect to the transaction itself.
- For transactions with substantial personal information exposure, diligence review of service provider agreements now must take into account privacy and security obligations in such agreements. This could apply across many company divisions, from HR to accounting/finance to customer relations.
- The parties should consider data privacy and security in the actual transaction process. Businesses may be making a ton of sensitive information accessible to other parties during the diligence process. Data room providers and other deal facilitators should be vetted for privacy and security just like any other vendor of the company.
- Buyers should consider whether a separate assessment of a target’s vendors is warranted and whether that assessment should be completed prior to or after closing.
Many of the challenges and lessons learned from the Report that apply to a business’s own vendors can apply to assessing a target’s vendor relationships as well:

Sellers that have addressed these factors in their vendor arrangements prior to diligence will likely have a faster and more efficient transaction.
Additional Privacy Regulation and Enforcement

As detailed in the Report, California and the EU have continued to dominate the privacy regulation landscape, but the past year saw plenty of updates in this area. In addition to California (twice), Virginia and Colorado jumped on the comprehensive privacy law bandwagon, while other states (such as Nevada and Texas) tweaked their existing, though somewhat limited, privacy laws. The New York State Department of Financial Services and other industry-specific cybersecurity regulators have also been particularly active in the past few years. Additionally, the international data privacy and security landscape continues to evolve as well with recent updates in China and proposed updates in many jurisdictions.
With all of these statutory and regulatory changes, M&A transactions (especially those with significant personal information exposure) are, by necessity, becoming increasingly sophisticated with respect to compliance with privacy laws. Not only will the transaction parties be subject to the privacy and security laws applicable to their own respective businesses, but the transaction itself may implicate certain privacy laws and regulations. Impacts of privacy laws on M&A transactions include:
- During diligence, targets should expect questions regarding data collection and use, as well as the location of employees and customers, as buyers look to evaluate (or confirm) applicable privacy regimes. Sellers with an understanding of applicable laws, and with data mapping and policies in place prior to diligence, can greatly expedite the transaction timeline.
- Buyers also must consider the impact of the proposed transaction on their own privacy compliance (especially for companies that currently fall below certain statutory thresholds).
- The parties should consider to what extent information sharing in diligence will implicate certain privacy laws, especially when using data rooms that may process information in different locations.
- Driven by specific requirements in certain privacy laws (like the CCPA), target companies should expect any public-facing privacy documentation (e.g., customer privacy policies) to be reviewed early in the diligence process.
- If gaps are identified, the parties should consider the impact on the deal and address what gets fixed prior to closing and what should be addressed post-closing.
- Representations in the transaction document may address specific privacy law requirements. If the deal contemplates representations and warranties insurance, the provider will likely have specific questions about privacy law compliance.
- The GDPR continues to be a major factor in cross-border M&A and transactions involving businesses with EU customers or employees. The decision in Schrems II and the corresponding updated guidance on cross-border data transfers have complicated transactions between EU and U.S. companies and can be a major factor in the transaction from initial diligence to post-closing transition.
Transaction parties that understand these statutory risks going into a proposed transaction will be better positioned to actually reach the finish line.