[author: Simon Varley]
Understanding what is the chain of suspicion in a legal setting is extremely important, especially when it comes to a digital forensic examiner. The chain of custody is suspicion for things like criminal defense work, especially when you’re trying to build a case. Simon Varley, the Director of Digital Forensics with Purpose Legal, is here to streamline this process and make it easier to understand.
Simon calls the technique of building the case and understanding the digital evidence of the opposite side “The Chain of Suspicion”. The primary idea behind this is to visualize and also sum up the discovery documents and forensic reports so the attorney can identify weaknesses in the opposing side’s presentation.
What is the Chain of Suspicion?
The Chain of Suspicion involves the process of reviewing all the law enforcement forensic reports and discovery documents. That way, the attorney will be able to visualize how this process took place and narrow down anything that could be used as a way to counteract the opposite side and their presentation.
Example: let’s take a website as an example, one that has insightful posts, bad content, and so on. However, law enforcement has been studying that website, and the site itself is a potential source of charges. In the discovery documents, you will see that law enforcement contacted the hosting provider or website owner. Furthermore, they asked for the visitor’s IP address or the IP that was used to set up the account.
That IP address becomes an identifier. And while the IP is not showcasing a name directly, you can go to the internet provider. Normally, a subscriber will receive an IP address, and the internet provider will keep a list of any IP addresses used.
Whenever law enforcement contacts the internet provider to share an IP, they can easily identify whose IP it is, and thus, they can easily come up with a name. Although some IP addresses are meant to be reused, if you have the date and time when the IP was used, you can track that down with the internet provider, be it AT&T, Verizon, or anyone else.
Are there other steps meant to be taken?
Once the law enforcement team goes to that establishment, they can get access to the Wi-Fi router. Of course, other steps could be taken here, like getting a search warrant. If a search warrant is acquired, then the law enforcement team will be able to access the device used to access that website at the specific hour stated in the discovery documents. On the laptop you can also find further incriminating evidence regarding the case as well.
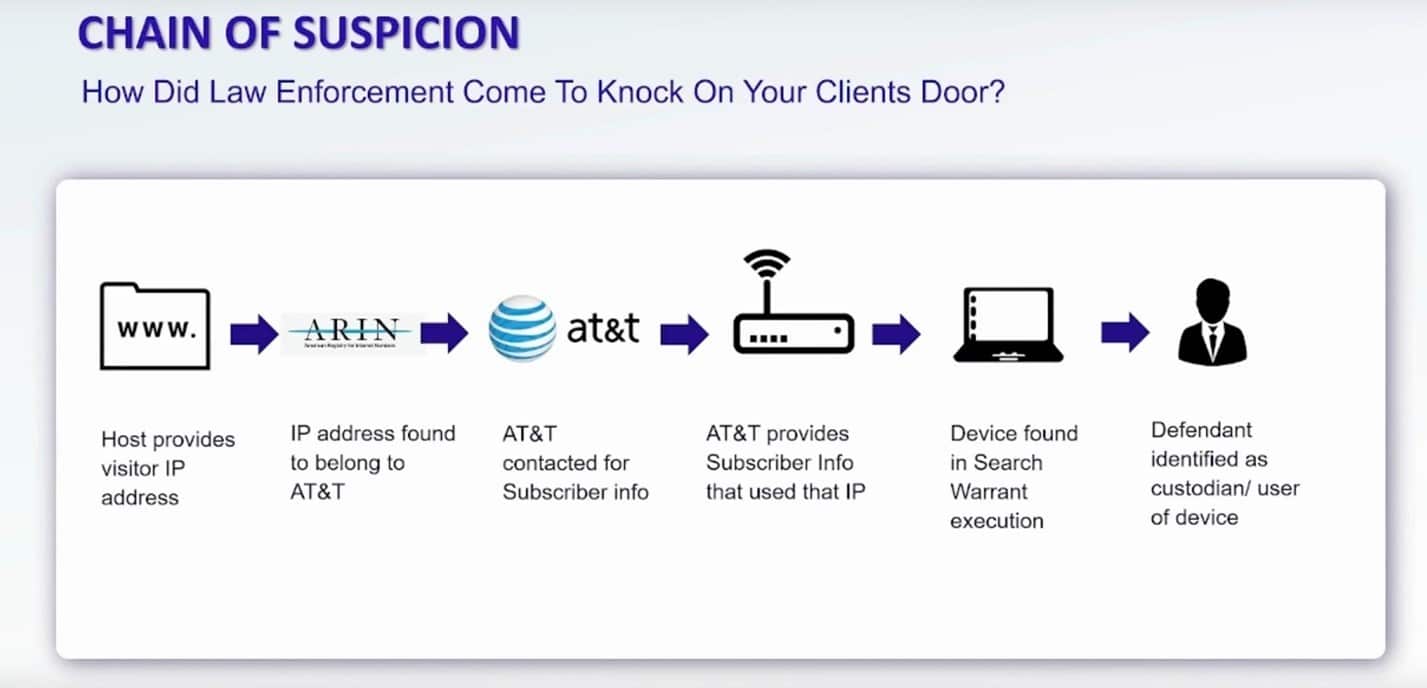
The law enforcement team will take the device, and lastly, they will place the defendant in front of the computer. During one case that Simon Varley worked on, a person was doing their taxes, and 30 minutes later they went to a bad website. They logged in an H&R Block, and it was very clear to the attorneys that based on the security measures and info provided the defendant was the one that accessed it.
What was received, and how was the data processed?
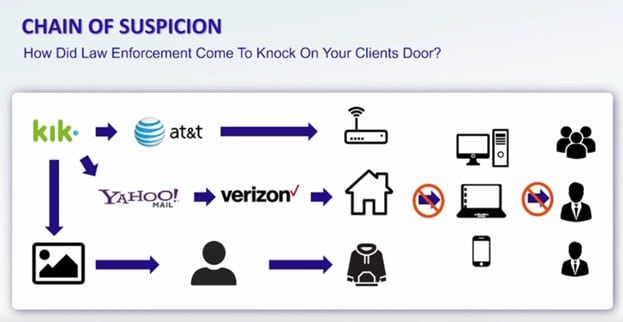
As you can see from the example above, not everything is laid out to the latest detail. Many different things need to be taken into account. In another example, the evidence against the defendant started with a chain based on an app named KIK. An account was set up, and then they contacted KIK to obtain the IP address that the defendant used.
AT&T owned the IP, so they went to them, and they showed the IP address in an effort to figure out who this belonged to. They received the name of Mr and Mrs Defendant, and after that, the law enforcement team went to Kik to find the email address, which in this case was a Yahoo email address. That required them to go to Yahoo, trying to find the IP of the person who logged into the Yahoo email.
Since the IP pertained to Verizon, they went to them, and Verizon was asked to show who was using that particular IP at the specified date and time. They received the same answer as the one they got from AT&T, it was Mr and Mrs Defendant. It’s also important to note that there was another avenue of evidence in this case, since the Kik charts had videos and images which resembled Mr Defendant.
The law enforcement team even matched an item the defendant owned with a dark hoodie (and white lettering) that he wore in the video. For most people, having three chains of evidence like the ones shown here would be more than enough. However, that’s not always the case. It might seem enough for someone who got on the case late. Yet you soon realize certain elements are missing.
Missing elements from the previous example
If you analyze this example in detail, you soon realize that there aren’t any devices identified in the discovery process. There’s no specific person that they had a positive identification for. Sure, there are some images and videos, but those offer a likeness, not definitive proof.
As a public defender, you always want to target weaknesses. In this case, since there’s no info about the people and devices, so that’s what you want to focus on. Maybe the law enforcement team didn’t want to pursue the situation more than that since they thought the evidence would be overwhelming.
More clues appear
From here, we can move onward to the discovery disclosures, stating what happened regarding the execution of the search warrant and what was on the Mr Defendant’s phone. Nothing was shared regarding that information, but it doesn’t mean all the devices had no information. Also, another thing noticed during this process is that there were 7 other males at the house during that time. So, it’s possible that one of those devices was used, and they were not collected.
Since 7 people and 12 devices were logged during that time, any of those devices could have been used to perform any malicious action. Getting all those devices would provide more clarity instead of just having the defendant’s likeness. The problem with the chain of custody is that the 2 main chains stop at the house, and as we can see, multiple people were there, so any of them could have been involved.
If we look at the Verizon plan, we discover the images and videos. The discovery process also documents what people were at that property when the investigators came with a search warrant. That’s when we find out the defendant had a brother who closely resembles Mr Defendant. Even if they are not twins, they have a similar hairstyle and build.
From the video, we see the person had a dark hoodie with the letters of the local University. The brother seems to have that hoodie, too, but in black, and it’s faded. The defendant has one in dark blue. Now, we can see that the chain might not be as powerful as one thought. The brother could have easily been mistaken for Mr Defendant. And it all matches: he is on the Verizon plan that the family has, he owns the same phone model, and he even owns the same clothing.
During the discovery process, it was also noted that the brother’s car was outside, and it had a stolen license plate. Once all these details add up, you can start building a case with all the information. But you always want to ensure details are certain, and any possible clue is followed as much as possible.
Conclusion
As you can see from these examples, the Chain of Suspicion can be very sneaky. A lot of the time, forensic reports will focus on the strong case. However, there will always be areas where you need to shine some light on, and if you do, you could find new evidence. Of course, there’s always the possibility that you won’t really find anything. But in the end, the thing that matters is to answer all the questions you have while pursuing any leads that arise.
The case mentioned above shows that if you just skim the data, it’s easy to say that Mr Defendant is at fault. But once you delve into the other details and study the situation more, you can see that he could have been mistaken for his brother. Even if these exercises might be time-consuming, they could help you get to the bottom line and solve the case.
As a forensic examiner, you always want to understand the case and study every single detail. You also need to show what is challengeable and not fully decided. Show everything from a different perspective, and that will help them through the discovery process.